Shadow Admins are the privilege paths you’re not watching. These accounts don’t belong to Domain Admins, but they can take over your environment anyway — thanks to ACL misconfigurations, GPO access, or SIDHistory abuse. If you're only auditing group membership, you're already exposed.
Tag: Identity Management
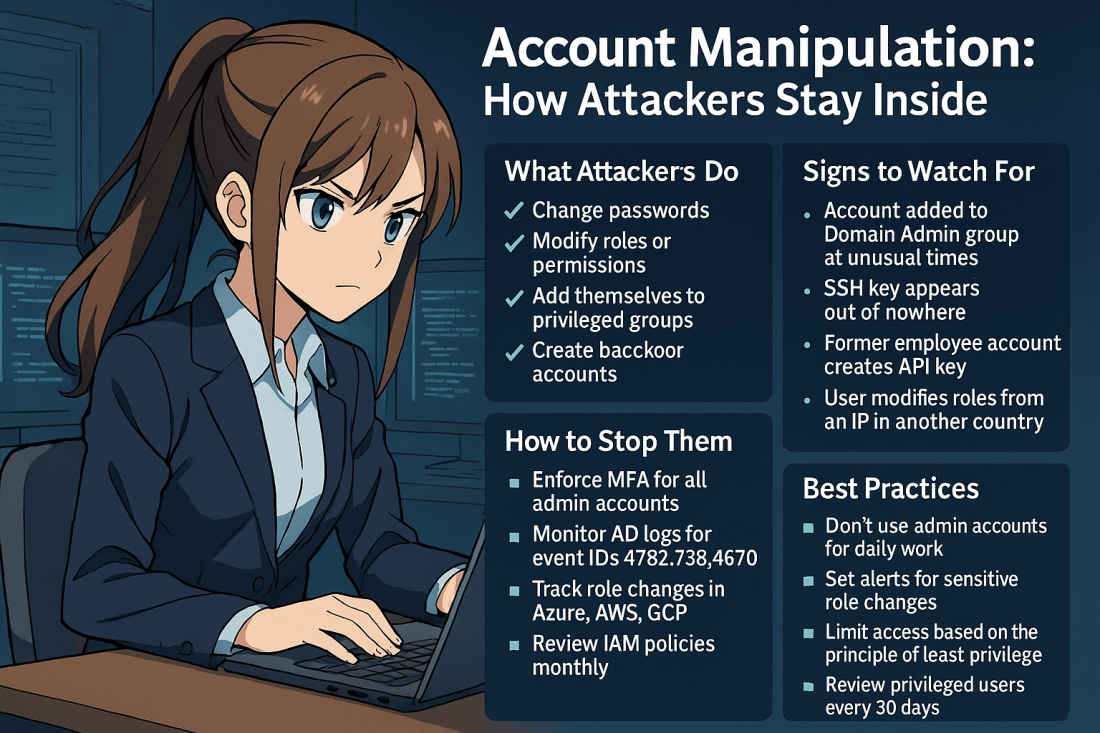
Account Manipulation: How Attackers Stay Inside Your Systems
Account manipulation is one of the stealthiest and most effective techniques used by threat actors to maintain or escalate access in compromised environments. Once inside, attackers often attempt to secure their foothold. They do this by modifying existing accounts. Another strategy is creating new ones that blend into your environment. This can include: Changing user … Continue reading Account Manipulation: How Attackers Stay Inside Your Systems