Despite improvements in Microsoft cloud security, lateral movement in hybrid Azure AD environments is still viable in 2025 — and often undetected.
Category: Microsoft Entra ID
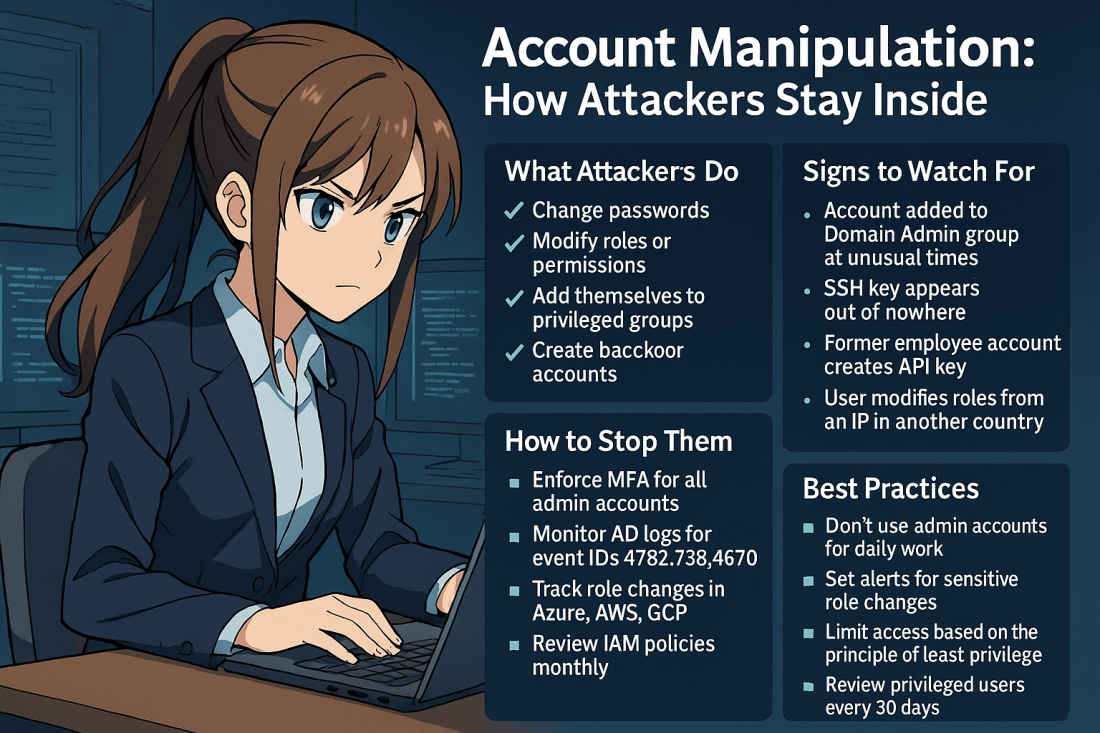
Account Manipulation: How Attackers Stay Inside Your Systems
Account manipulation is one of the stealthiest and most effective techniques used by threat actors to maintain or escalate access in compromised environments. Once inside, attackers often attempt to secure their foothold. They do this by modifying existing accounts. Another strategy is creating new ones that blend into your environment. This can include: Changing user … Continue reading Account Manipulation: How Attackers Stay Inside Your Systems
Migrating Your Windows Device from Active Directory to ENTRA ID
In a world where mobility is crucial, maintaining an AD joined computer can change from an asset to a burden. Modern users are constantly on the move. They do not rely on applications that need a constant remote connection. These users often manage a device tethered to an on-premise infrastructure. Instead of simplifying their daily … Continue reading Migrating Your Windows Device from Active Directory to ENTRA ID
Steps to Migrate to New Authentication Techniques
Prepare the migration Beginning September 30, 2025, authentication techniques can't be managed in these legacy multi-factor authentication and self-service password reset policies. Before start the migration of the new authentication techniques you need to review the action configuration of: Multi-factor Authentication Policy S.S.P.R. Policy Review the legacy MFA policy Start by documenting which techniques are … Continue reading Steps to Migrate to New Authentication Techniques