Even after uninstalling Exchange, traces of its deep integration with Active Directory remain — powerful groups, lingering ACLs, legacy attributes, and automation leftovers. Whether Exchange is running or long gone, ignoring what it left behind could leave your domain exposed. Here's what you need to know (and clean up) before someone else does
Category: Microsoft 365
Lateral Movement in Azure AD: What Still Works in 2025
Despite improvements in Microsoft cloud security, lateral movement in hybrid Azure AD environments is still viable in 2025 — and often undetected.
All-in on Cloud? Yes—but with your feet on the ground
Introduction Cloud technology is no longer a novelty — it’s the new normal. In recent years, more and more companies have been completing their shift from on-premise infrastructures to fully cloud-based environments. Not just for email or storage, but for core infrastructure, development environments, business data, and workflows. And yet, there’s still some hesitation. Some … Continue reading All-in on Cloud? Yes—but with your feet on the ground
Quantum Computing and Cybersecurity: How Companies Can Prepare for the Quantum Wave
Introduction The tech world is quietly approaching a disruptive moment: the rise of quantum computing.This isn’t science fiction or something that only concerns physicists in lab coats. It's a technology that, once mature, could undermine the entire foundation of today’s cybersecurity—from encrypted emails to digital signatures, VPNs, and even blockchain. But why is that? And … Continue reading Quantum Computing and Cybersecurity: How Companies Can Prepare for the Quantum Wave
Pass-the-Hash (PtH): Attack Technique and Complete Defenses
What is Pass-the-Hash? Pass-the-hash (PtH) is an attack technique that allows an attacker to authenticate to a remote system using the password hash, without the need for the password in plain text. It is particularly effective in Windows environments, where the NTLM authentication protocol allows authentication using static hashes. How the attack works Initial access … Continue reading Pass-the-Hash (PtH): Attack Technique and Complete Defenses
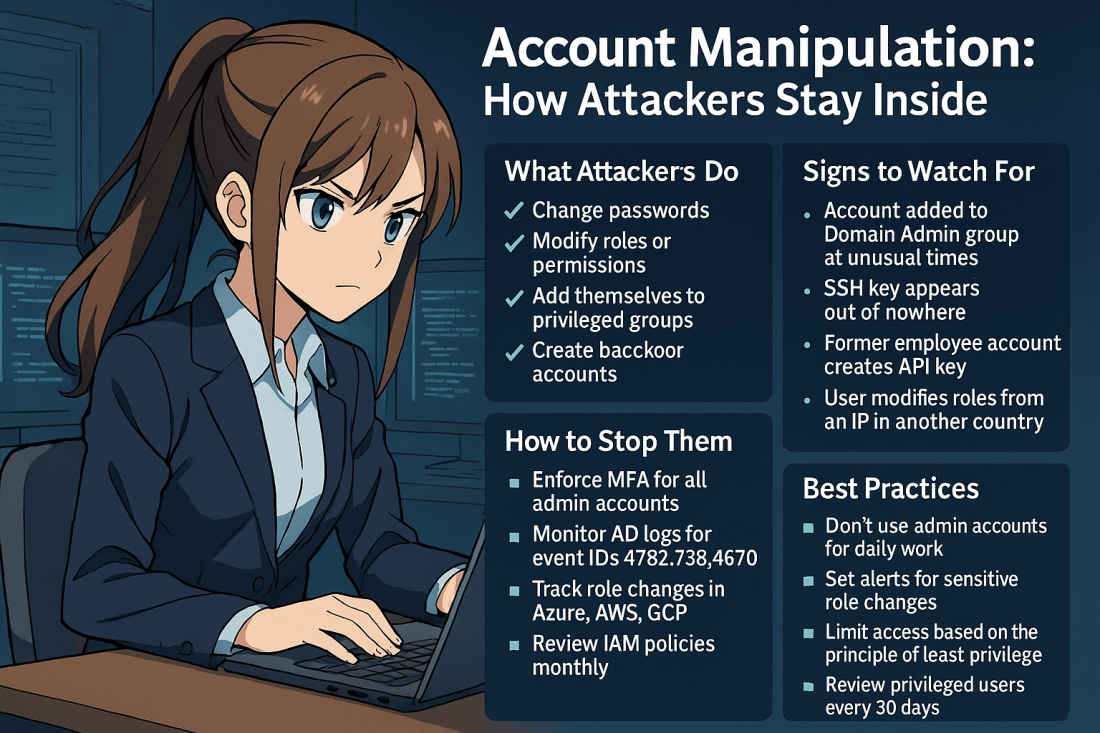
Account Manipulation: How Attackers Stay Inside Your Systems
Account manipulation is one of the stealthiest and most effective techniques used by threat actors to maintain or escalate access in compromised environments. Once inside, attackers often attempt to secure their foothold. They do this by modifying existing accounts. Another strategy is creating new ones that blend into your environment. This can include: Changing user … Continue reading Account Manipulation: How Attackers Stay Inside Your Systems
Steps to Migrate to New Authentication Techniques
Prepare the migration Beginning September 30, 2025, authentication techniques can't be managed in these legacy multi-factor authentication and self-service password reset policies. Before start the migration of the new authentication techniques you need to review the action configuration of: Multi-factor Authentication Policy S.S.P.R. Policy Review the legacy MFA policy Start by documenting which techniques are … Continue reading Steps to Migrate to New Authentication Techniques
How to Use Microsoft Booking for Seamless Appointments
What is Microsoft Booking? Microsoft Booking is an appointment scheduling and booking software offered by Microsoft. It is designed to help businesses manage and streamline their appointment scheduling processes. With Microsoft Booking, customers can easily schedule and manage appointments with a business or service provider online. Features Online booking: you can view available time slots … Continue reading How to Use Microsoft Booking for Seamless Appointments
Windows LAPS: Transition from Legacy to Modern Password Management
The legacy Microsoft LAPS product is deprecated as of Windows 11 23 H2 and later. The installation of the legacy Microsoft LAPS MSI package is blocked on newer versions of the operating system. Microsoft will no longer consider code changes for the legacy Microsoft LAPS product. Microsoft recommends using Windows LAPS to manage local administrator … Continue reading Windows LAPS: Transition from Legacy to Modern Password Management