AI is not the end of thinking. It is the triumph of the average. In a world where predictability is more valuable than originality, genius becomes a statistical error and artificial intelligence the perfect tool to normalize it.
Author: Marco Nasta
OSINT: The Art of Discovering Everything About Anyone (Legally)
In a world where data never sleeps, every trace we leave online becomes a clue. OSINT — Open Source Intelligence — turns open information into power. From social media footprints to forgotten metadata, digital investigators learn to see what others overlook. No hacking, no intrusion — just the art of connecting dots in the endless sea of data.
Social Engineering: How Hackers Trick You Without Touching a Line of Code
You don’t need malware to hack someone — just a good story. From Kevin Mitnick’s classic tricks to today’s AI-powered scams, social engineering proves one thing: people are still the weakest link in cybersecurity.
The Ghosts of Exchange: Hidden Permissions Lurking in Active Directory
Even after uninstalling Exchange, traces of its deep integration with Active Directory remain — powerful groups, lingering ACLs, legacy attributes, and automation leftovers. Whether Exchange is running or long gone, ignoring what it left behind could leave your domain exposed. Here's what you need to know (and clean up) before someone else does
Lateral Movement in Azure AD: What Still Works in 2025
Despite improvements in Microsoft cloud security, lateral movement in hybrid Azure AD environments is still viable in 2025 — and often undetected.
Shadow Admins in Active Directory: The Privilege You Don’t See (Until It’s Too Late)
Shadow Admins are the privilege paths you’re not watching. These accounts don’t belong to Domain Admins, but they can take over your environment anyway — thanks to ACL misconfigurations, GPO access, or SIDHistory abuse. If you're only auditing group membership, you're already exposed.
Kerberoasting: How It Works, How to Defend, and How to Minimize the Damage
Learn how Kerberoasting exploits Kerberos authentication in Active Directory, how it works, and what steps you can take to defend against it.
All-in on Cloud? Yes—but with your feet on the ground
Introduction Cloud technology is no longer a novelty — it’s the new normal. In recent years, more and more companies have been completing their shift from on-premise infrastructures to fully cloud-based environments. Not just for email or storage, but for core infrastructure, development environments, business data, and workflows. And yet, there’s still some hesitation. Some … Continue reading All-in on Cloud? Yes—but with your feet on the ground
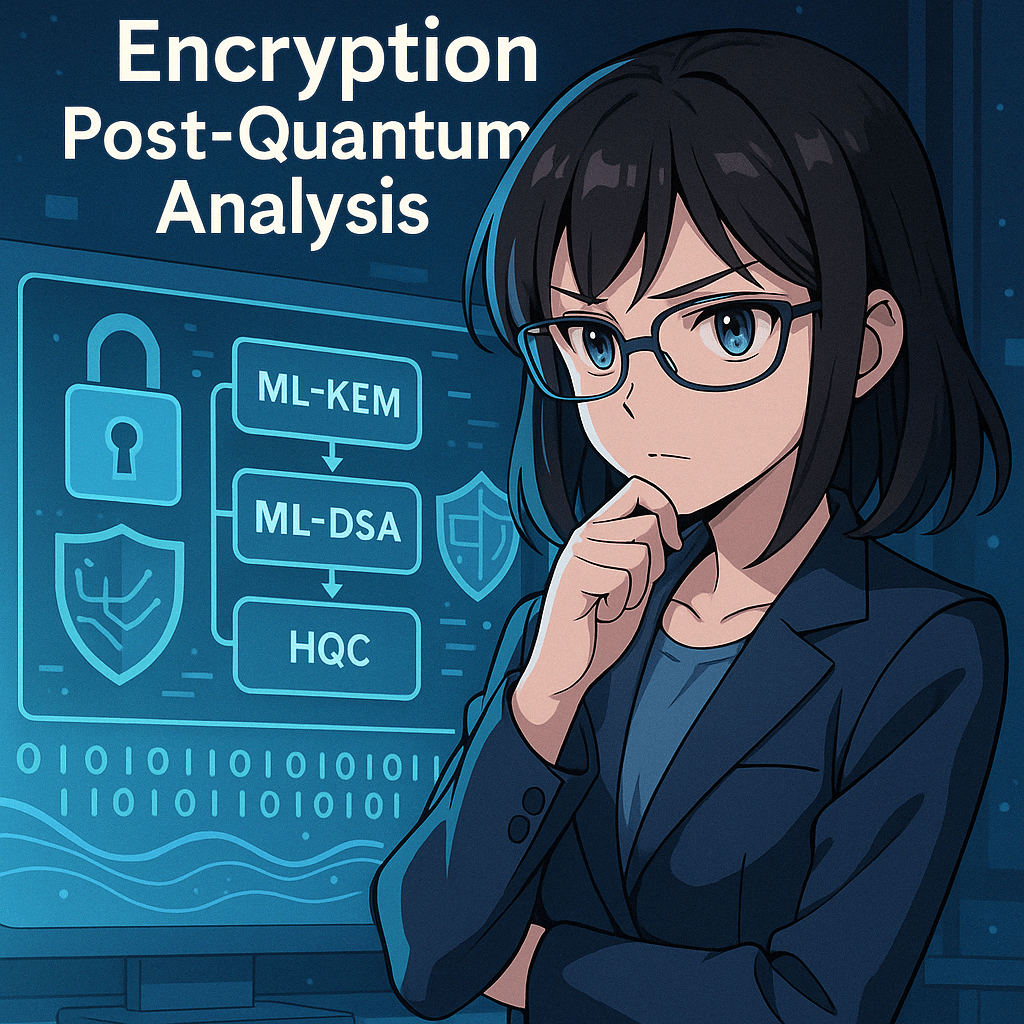
Quantum Computing and Cybersecurity: How Companies Can Prepare for the Quantum Wave
Introduction The tech world is quietly approaching a disruptive moment: the rise of quantum computing.This isn’t science fiction or something that only concerns physicists in lab coats. It's a technology that, once mature, could undermine the entire foundation of today’s cybersecurity—from encrypted emails to digital signatures, VPNs, and even blockchain. But why is that? And … Continue reading Quantum Computing and Cybersecurity: How Companies Can Prepare for the Quantum Wave
Pass-the-Hash (PtH): Attack Technique and Complete Defenses
What is Pass-the-Hash? Pass-the-hash (PtH) is an attack technique that allows an attacker to authenticate to a remote system using the password hash, without the need for the password in plain text. It is particularly effective in Windows environments, where the NTLM authentication protocol allows authentication using static hashes. How the attack works Initial access … Continue reading Pass-the-Hash (PtH): Attack Technique and Complete Defenses
Tiering in Active Directory: Effective Strategy to Increase Security and Resiliency
Active Directory (AD) is the beating heart of identity and IT asset management in many organizations. Being a critical system, the AD frequently becomes the target of cyber attacks aimed at gaining elevated privileges or compromising entire corporate infrastructures. For this reason, tiering has become a critical approach to reducing risk and ensuring greater security … Continue reading Tiering in Active Directory: Effective Strategy to Increase Security and Resiliency
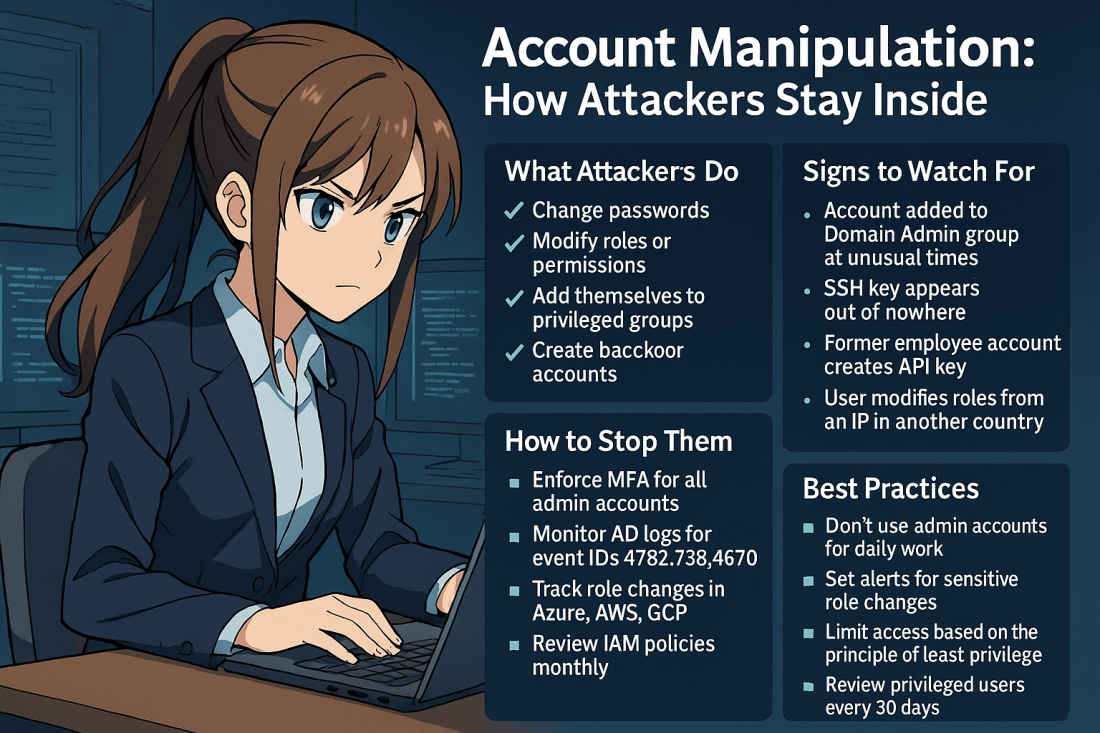
Account Manipulation: How Attackers Stay Inside Your Systems
Account manipulation is one of the stealthiest and most effective techniques used by threat actors to maintain or escalate access in compromised environments. Once inside, attackers often attempt to secure their foothold. They do this by modifying existing accounts. Another strategy is creating new ones that blend into your environment. This can include: Changing user … Continue reading Account Manipulation: How Attackers Stay Inside Your Systems
Windows Domain Name Service Remote Code Execution Vulnerability (CVE-2025-24064)
CVE-2025-24064 of March 11, 2025 highlights the possibility of executing malicious code on the network by exploiting the Use After Free vulnerability in the DNS server. The vulnerability shows the importance of allowing DNS updates only from trusted devices and therefore having only secure updates, preventing unrecognized devices from updating or adding their A record … Continue reading Windows Domain Name Service Remote Code Execution Vulnerability (CVE-2025-24064)
Step-by-Step C# PowerShell Module Creation in Visual Code
Prerequisites You need to have at least the next tools: Visual Studio Code .NET Framework Developer Pack 4.7.2 PowerShell 5.1 Create a Class Library Project in the .NET Framework The first step is to create a Class Library in the .NET Framework 4.7.2, compatible with PowerShell 5.1 generating the MyPowerShellModule.csproj file. Open a PowerShell terminal … Continue reading Step-by-Step C# PowerShell Module Creation in Visual Code
Migrating Your Windows Device from Active Directory to ENTRA ID
In a world where mobility is crucial, maintaining an AD joined computer can change from an asset to a burden. Modern users are constantly on the move. They do not rely on applications that need a constant remote connection. These users often manage a device tethered to an on-premise infrastructure. Instead of simplifying their daily … Continue reading Migrating Your Windows Device from Active Directory to ENTRA ID