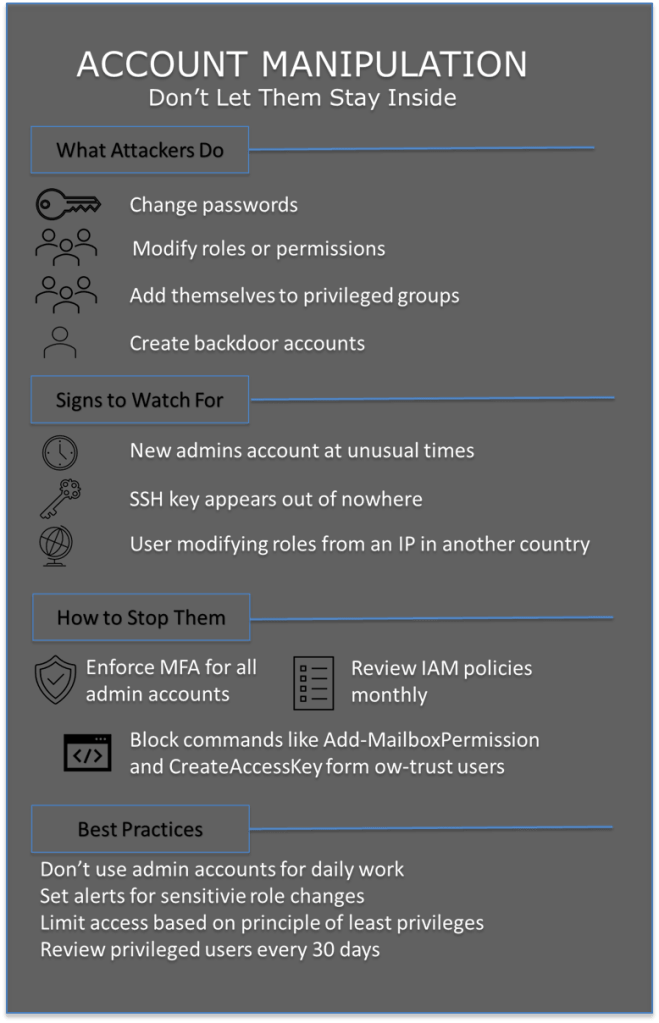
Account manipulation is one of the stealthiest and most effective techniques used by threat actors to maintain or escalate access in compromised environments. Once inside, attackers often attempt to secure their foothold. They do this by modifying existing accounts. Another strategy is creating new ones that blend into your environment.
This can include:
- Changing user credentials
- Assigning elevated privileges to a compromised account
- Creating new “shadow” accounts with high privileges
- Bypassing security controls, like password expiration policies
The goal? Stay undetected and in control for as long as possible.
How to Detect Account Manipulation Attempts
1. Changes in Active Directory
- Watch for unauthorized modification of AD objects or group memberships
- Watch for the enrollment of new device, especially if MFA is not enforced
Example: A workstation is joined to the domain at 2:45 AM using an account typically used by an HR employee.
2. Cloud Environment Abuse (Azure, AWS, GCP)
- Track suspicious IAM role assignments
- Detect the creation of access keys or login profiles from unusual accounts
- Observe changes to service principals or certificate secrets
Example: A former contractor’s account generates a new access key in AWS weeks after termination.
3. Suspicious Command or API Usage
- Review usage of commands like authorized_keys, sshd_config, or Add-MailboxPermission
- Investigate unusual CLI/API calls, e.g., CreateLoginProfile, GetFederationToken, CreateAccessKey
Example: A low-privilege account imports a new SSH key into an EC2 instance that’s not typically accessed remotely.
4. Key Security Events to Watch
- Event ID 4738 – User account changed
- Event ID 4728 – Account added to a privileged group
- Event ID 4670 – Permissions changed on an object
Example: A marketing team account is added to the “Domain Admins” group early Saturday morning.
Mitigation Strategies
Multi-Factor Authentication
- Enforce MFA across all user and privileged accounts
- Avoid relying solely on password-based authentication
Network Segmentation
- Isolate critical systems using VLANs, firewalls, and DMZs
- Separate cloud workloads using Virtual Private Cloud (VPC) instances
Privileged Account Management
- Avoid using domain or root accounts for day-to-day tasks
- Use just-in-time (JIT) access and remove persistent privileges
Restrict File and Directory Permissions
- Secure sensitive files related to authentication or account management
- Avoid overly broad file permissions for system directories
Secure Operating System Configuration
- Turn off unnecessary services (e.g., SMB)
- Harden domain controllers and enforce security baselines
User Account Governance
- Regularly review account permissions and group memberships
- Prevent standard users from modifying accounts or policies
Remove Vulnerable or Unused Features
- Remove outdated or unnecessary software and tools
- Reduce the attack surface by disabling exploitable authentication mechanisms
Conclusion: Subtle, Persistent, and Dangerous
Account manipulation is not always obvious. It doesn’t require zero-days or loud lateral movement—it’s a quiet, methodical process. Attackers rely on blending in and exploiting gaps in identity management.
Defensive focus should be on:
- Correlating unusual account behavior
- Deploying smart alerting based on context (user role, time, device)
- Securing identity infrastructure across hybrid environments
Digital identity is no longer just about access—it is the new attack surface.