Secure Boot Security Feature Bypass Vulnerability (CVE-2023-24932) is a Security Vulnerability released on May 9, 2023. It allowed an attacker who successfully exploited this vulnerability to bypass Secure Boot on devices. To exploit the vulnerability, an attacker needs physical access or administrative rights to a target device. The attacker then install an affected boot policy.
Mitigation against this security vulnerability are included in the Windows security updates. These updates were released on or after July 9, 2024.
But, these mitigation are not enabled by default.
- Secure Boot is recommended by Microsoft for creating a safe and trusted path. This path extends from the Unified Extensible Firmware Interface (UEFI) through the Windows kernel Trusted Boot sequence.
- Secure Boot helps prevent bootkit malware in the boot sequence.
- Disabling Secure Boot puts a device at risk of being infected by bootkit malware.
You should decide whether you have to allow the mitigation or wait for a future update from Microsoft.
If you choose to allow the mitigation, you must verify your devices are updated and ready, and understand the risks.
All Windows devices running next operating systems with Secure Boot protections enabled are affected by the BlackLotus bootkit.
- Windows 10 Version 1507 32-bit Systems, x64-based Systems affected from 10.0.10240.0 before 10.0.10240.20710
- Windows 10 Version 1607 32-bit Systems, x64-based Systems from 10.0.14393.0 before 10.0.14393.7159
- Windows 10 Version 1809 32-bit Systems, x64-based Systems from 10.0.17763.0 before 10.0.17763.6054
- Windows 10 Version 1809 ARM64-based Systems from 10.0.0 before 10.0.17763.6054
- Windows 10 Version 20H2 32-bit Systems, ARM64-based Systems from 10.0.0 before 10.0.19042.2965
- Windows 10 Version 21H2 32-bit Systems, ARM64-based Systems, x64-based Systems from 10.0.19043.0 before 10.0.19044.4651
- Windows 10 Version 22H2 x64-based Systems, ARM64-based Systems, 32-bit Systems affected from 10.0.19045.0 before 10.0.19045.4651
- Windows 11 Version 23H2 x64-based Systems affected from 10.0.22631.0 before 10.0.22631.4890
- Windows 11 Version 24H2 ARM64-based Systems, x64-based Systems from 10.0.26100.0 before 10.0.26100.3194
- Windows 11 version 21H2 x64-based Systems, ARM64-based Systems from 10.0.22000.0 before 10.0.22000.3079
- Windows 11 version 22H2 ARM64-based Systems, x64-based Systems affected from 10.0.22621.0 before 10.0.22621.4890
- Windows 11 version 22H3 ARM64-based Systems affected from 10.0.22631.0 before 10.0.22631.4890
- Windows Server 2008 R2 Service Pack 1 (Server Core installation) x64-based Systems from 6.1.7601.0 before 6.1.7601.27219
- Windows Server 2008 R2 Service Pack 1 x64-based Systems affected from 6.1.7601.0 before 6.1.7601.27219
- Windows Server 2008 Service Pack 2 (Server Core installation) 32-bit Systems, x64-based Systems from 6.0.6003.0 before 6.0.6003.22769
- Windows Server 2008 Service Pack 2 32-bit Systems from 6.0.6003.0 before 6.0.6003.22769
- Windows Server 2008 Service Pack 2 x64-based Systems from 6.0.6003.0 before 6.0.6003.22769
- Windows Server 2012 (Server Core installation) x64-based Systems from 6.2.9200.0 before 6.2.9200.24975
- Windows Server 2012 R2 (Server Core installation) x64-based Systems from 6.3.9600.0 before 6.3.9600.22074
- Windows Server 2012 R2 x64-based Systems from 6.3.9600.0 before 6.3.9600.22074
- Windows Server 2012 x64-based Systems from 6.2.9200.0 before 6.2.9200.24975
- Windows Server 2016 (Server Core installation) x64-based Systems from 10.0.14393.0 before 10.0.14393.7159
- Windows Server 2016 x64-based Systems from 10.0.14393.0 before 10.0.14393.7159
- Windows Server 2019 (Server Core installation) x64-based Systems from 10.0.17763.0 before 10.0.17763.6054
- Windows Server 2019 x64-based Systems from 10.0.17763.0 before 10.0.17763.6054
- Windows Server 2022 x64-based Systems from 10.0.20348.0 before 10.0.20348.2582
- Windows Server 2022, 23H2 Edition (Server Core installation) x64-based Systems affected from 10.0.25398.0 before 10.0.25398.1009
- Windows Server 2025 x64-based Systems from 10.0.26100.0 before 10.0.26100.3194 Windows Server 2025 (Server Core installation) x64-based Systems from 10.0.26100.0 before 10.0.26100.3194
TAKE ACTION
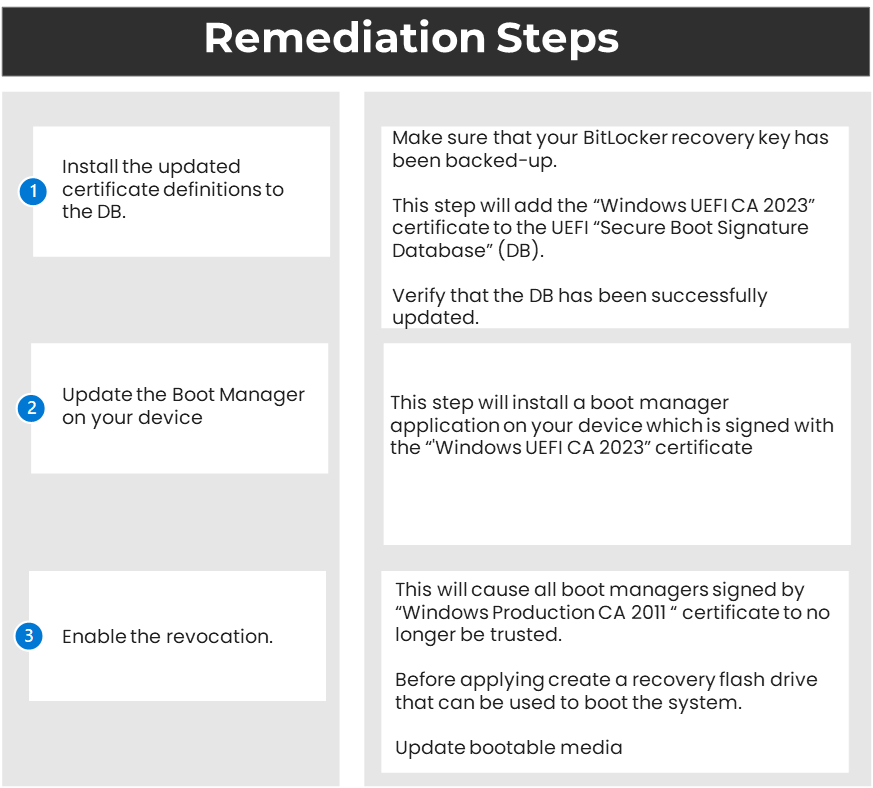
- Phase 1: In this phase, install the Windows monthly security update. The update should be released on or after July 9, 2024. Make sure it is installed on supported Windows devices. These updates include mitigation for CVE-2023-24932 but are not enabled by default.
- Phase 2: Review the updated schedule. Start testing the first two mitigation against representative devices from your environment. Start planning for the deployment.
- Phase 3: Start testing the third mitigation that untrusts the signing certificate used for all earlier Windows boot managers.
Mitigation Steps
Known Issues
- TPM 2.0: The systems that run Windows Server 2012 and Windows Server 2012 R2 cannot deploy the mitigation. These mitigation were released in the July 9, 2024 security update. They face known compatibility issues with TPM measurements. The July 9, 2024 security updates will block mitigation #2 (boot manager) and #3 (DBX update) on affected systems.
- Device Firmware: Not all device firmware will successfully update the Secure Boot DB or DBX. Please contact the device manufacturer for firmware updates. If the device is not in support, Microsoft recommends upgrading the device.
- Symantec Endpoint Encryption: Secure Boot mitigation can’t be applied to systems who have installed Symantec Endpoint Encryption. Microsoft and Symantec are aware of the issue and will be addressed in future update.
Conclusion
| What Microsoft is doing | What you should do |
| Rolled out replacement signing certificates with new Microsoft Windows UEFI CA 2023 | Follows the steps in KB5036210 to add the new Windows trust anchor |
| Current trust anchors Microsoft Windows Production PCA 2011 currently used to authorize trust for all Windows boot managers in Secure Boot will expire in 2026 | [Optionally] revoke trust in the Windows Production PCA 2011. |